An Intrusion (1) System (IDS) is a system that monitons network traffic for suspicious activity and alerts when such activity is discovered While (2) detection and reporting are the primary funcitons of an IDS,some IDSs are also capable of taking actions when (3) activity or anomalous traffic is detected, including(4)traffic sent from suspicious Internet Protocol(IP)addresses,Any malicious venture or violation is normally reported either to anadministretor or collected centrally using a(5) information and event management(SIEM)system.A SIEM system integrates outputs from multiple sources and uses alarm filtering techniques to differentiate malicious actvity from false alarms.
问题1:
A.Detection
B.Defending
C.Definition
D.Descripiton
问题2:
A.connection
B.anomaly
C.action
D.error
问题3:
A.normal
B.frequent
C.malicious
D.known
问题4:
A.receiving
B.blocking
C.replying
D.storing
问题5:
A.status
B.service
C.security
D.section
在几种不同类型的软件维护中,通常情况下()所占工作量最大。
在()中,项目经理的权力是最小的。
在项目实施的过程中,项目经理通过项目周报中的项目进度分析图表发现机房施工进度有延期风险。项目经理立即组织相关人员进行分析,下达了关于改进措施的书面指令。该指令属于( )
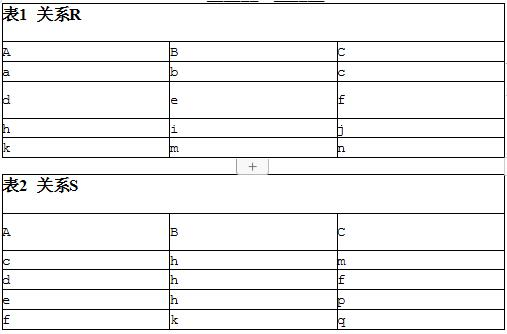
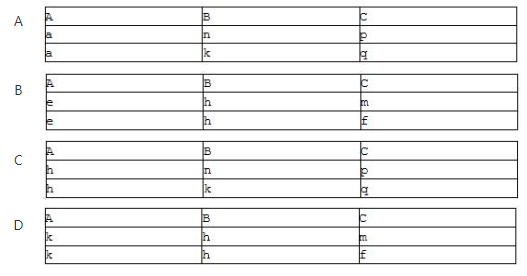

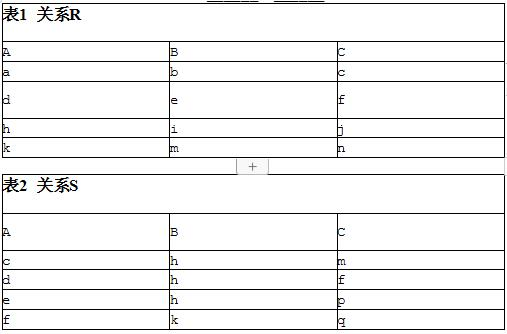
The IT service manager resigns from a project that meets the scheduleand budget. After hiring an alternativenew manager, the team is opposed to the comments from the new manager. The team is at () developmentstages。
()is closet to Deming's definition of Quality。
The IT service manager has learned that a software canimprove the efficiency of current and future project tasks. Because the software is fresh to the Company. Theengineer is not familiar with the software. The lT service manager decides to send the highest level engineero attend the external training course. The proiect manager uses () risk strategies。
The process control charts are used ()。